Tilting at Wind Farm Portals - a Modern Day Quixotic Challenge
Table of Contents
by:
Lari Huttunen

In late 2018 I mounted my trusty steed Rocinante on a quest to expose hordes of ugly giants and peruse the ever changing face of public exposure. Of course my steed, python, is not an animal but a programming language, which in this case needs a steady course of Shodan dorks as its daily staple. Once fed, the automation spins out an endless stream of those in need of help, who themselves are oblivious to danger.
One of these amassed dangers relates to publicly exposed wind farm management portals, which date back at least to 2013, when ICS-CERT first warned of an XSS flaw in a web-based management application. As in many cases, the XSS was just an icing on the cake related to product security, whereas the real problems lie in the field of operational security. If there is no plan to patch or test the application and the deployment is done haphazardly, then the result is likely a recipe for disaster.
I mean, who in their right mind would deploy a wind farm management portal application so that it is accessible from the whole Internet?

What is a wind farm management portal? #
It is a web-based application which allows you to monitor and control the wind farm operations over the Internet. The idea is sound if the deployment is done correctly, i.e. the access to the portal is controlled via a VPN or firewall. It is not even intended to be used over the Internet for which we have many clues.
One of those clues is the X.509 Subject CN field of the deployed applications:
Subject: C=DE, ST=Hamburg, L=Hamburg, O=Nordex, OU=CE\/SDO,
CN=127.0.0.1, CN=172.17.0.212, CN=172.17.0.211, CN=192.168.8.212,
CN=192.168.8.211
After all, using localhost or RFC 1918 addresses in the certificate does not speak of an application deployed with the needs of the Internet in mind, now does it?
Originally I thought that the application was used just for monitoring purposes, but then I discovered a version of the operating manual which proved me wrong.
Nordex SE, NDX1 #
Nordex SE is a European company that designs, sells and manufactures wind turbines. The company’s headquarters is located in the German city of Rostock while management is situated in Hamburg.
Despite having roughly 4 billion USD in revenue and 43 million of operating income in 2017, it is evident that they have invested very little in the cybersecurity of their company or their product. Another clue to this effect is the fact that they got ransomwared in 2022 and for a while had to shut down their operations. This combined with the fact that they provide remote operational support for their customers, does not really make you sleep sound at night either.
I mean, would you like to live next to a wind farm, whose rotors can be remotely controlled by let’s say a teenager in a basement in Sao Paulo, whilst playing Rainbow Six Siege and hacking on the side just for the lulz? Not to mention the kind of havoc a dedicated threat actor could wreak on the exposed wind farms all over Europe in this day and age.
Tilting at Wind Farms #
Often trying to help those who need help is a tiresome task, as our attempts to directly contact the company were met only with the continuous whir of turbines churning out energy for the power hungry electricity grid. We tried calling their Finnish office, emailing them, as well as contacting their top management through LinkedIn.
No answer.
Once More unto the Breach with the Help of NCSC-FI #
For more than a year we have shared all of our research data in real-time with NCSC-FI who have done their best to share the findings with their peers mostly in Europe. The results have been varying, but at least we have done our utmost best to get the information out there. The whack-a-mole game has kept NCSC-FI entertained and most if not all of the wind farm portals in Finland have been taken out of the reach of the whole Internet.
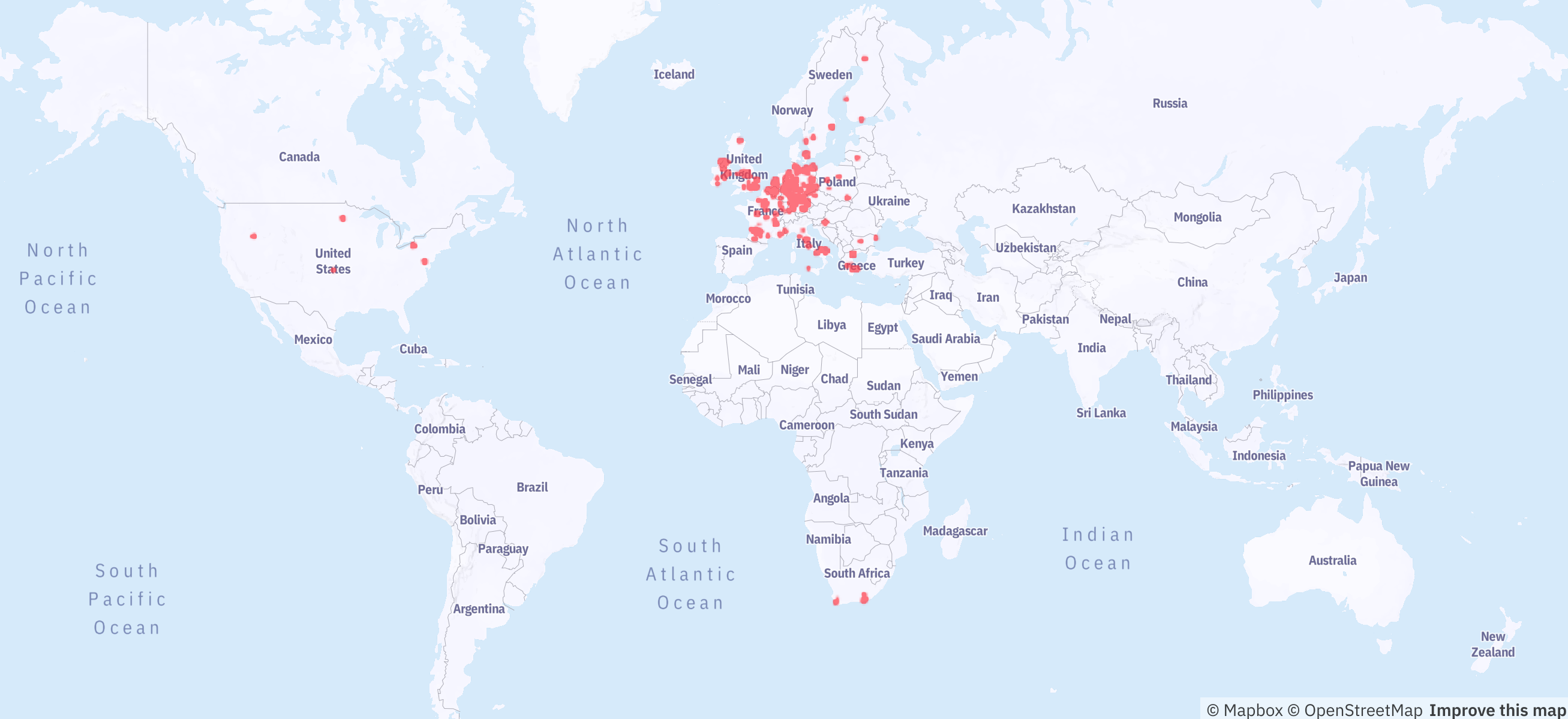
Status Quo #
The current situation, however, is far from perfect which is one of my main motivations for finally publishing this write-up. I have been sitting on it for more than two years, but finally I have come to the conclusion that it is better to try to raise awareness than sit in silence and do nothing. Hopefully, this information will help the Nordex customers raise this question with the vendor before all hell breaks loose.
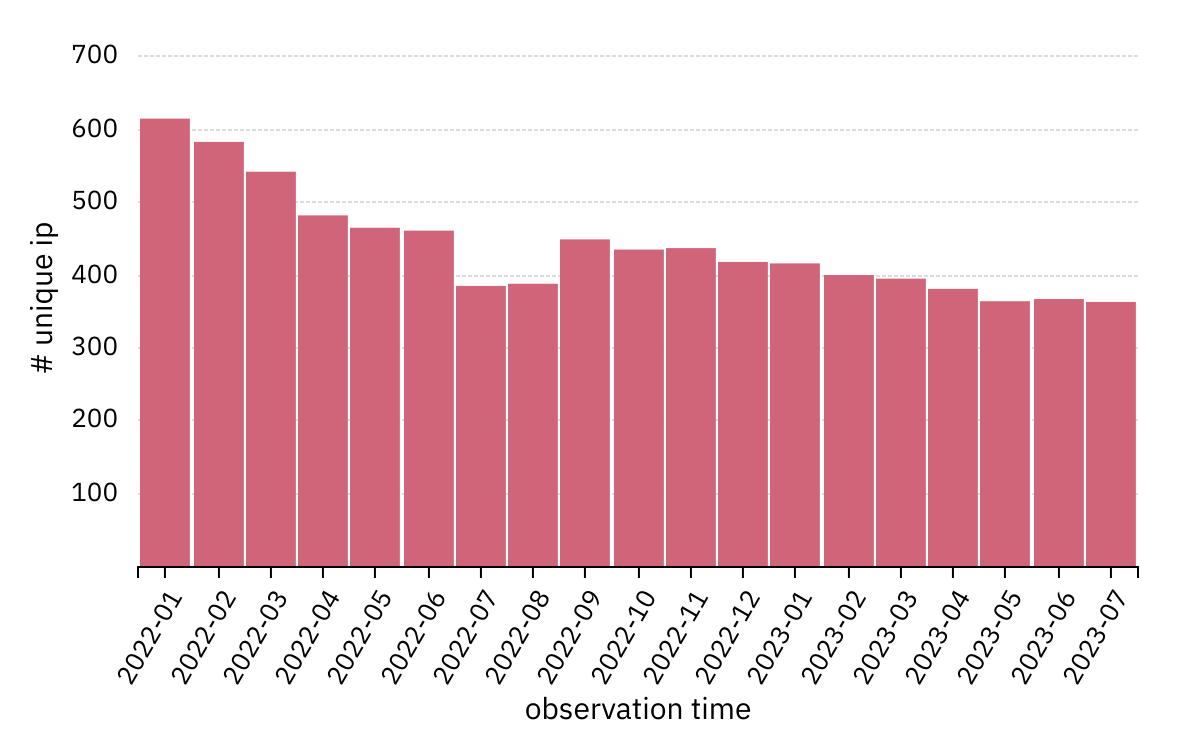
The only actual way I think this problem can be solved is that Nordex SE learns to implement proper product and operational security measures for their customers. A testament to the fact is an old wind farm deployment I discovered, which had vulnerabilities dating back to 2004 as well as being completely naked out there – waiting to be abused.
Issues at Hand #
In summary, I would like to outline three things that must happen before things will start getting better:
- The exposed wind farm portals must be taken off the Internet, period.
- Nordex SE will need to make it mandatory for new deployments to be firewalled off the internet and/or placed behind a VPN.
- Product security is an ongoing activity, which means that the management platform needs to be updatable. At present, it seems that only new deployments get newer software versions.
Credits #
- The hero image courtesy of Nicholas Doherty on Unsplash.